The DatoCMS Blog
Even more control for your sensitive projects: introducing Audit Logs
Today, we're happy to publicly release another vital feature for our Enterprise customers and fast growing startups: Audit Logs.
The system we developed offers every detail of any action performed inside DatoCMS. It is filterable, exportable, and accessible via API:
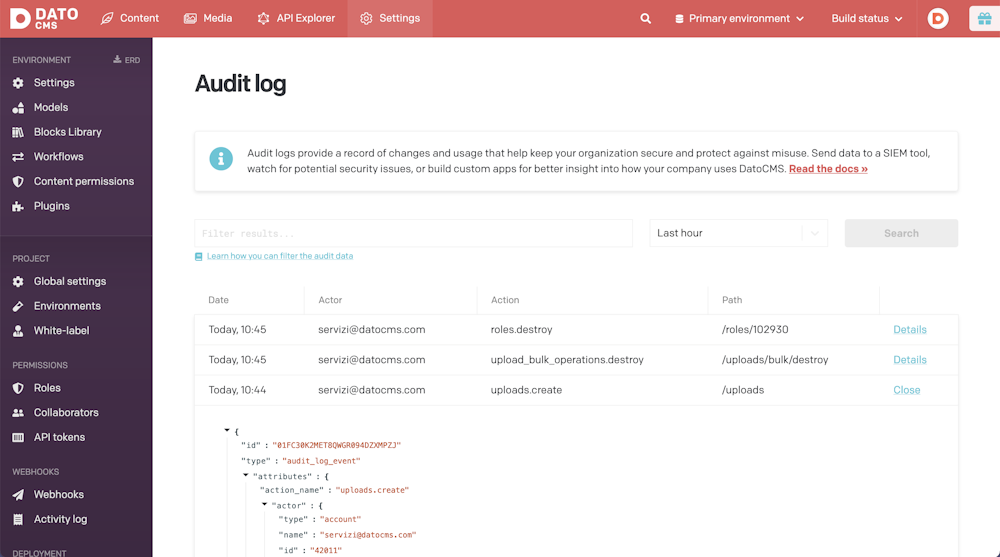
What is an Audit Log?
Audit Logs are a valuable resource for admins and auditors who want to examine suspicious activity or diagnose and troubleshoot issues. Also called "audit trail", they take note of just about every change within a system, and provide a complete track record of your system’s operations.
Advantages of Audit Logs
These logs can give both IT teams and businesses invaluable insight into what behaviour is normal and what behaviour isn’t.
Improved Security
Audit logs help with security because they provide records of all IT activity, including suspicious activity. Event log auditing is also important for cybersecurity because it provides records that can serve as evidence. A comprehensive and in-depth log audit can make all the difference in the event of a legal battle and can protect your business from liability.
Proving Compliance
Externally, audit logs are critical for proving compliance with common regulations like HIPAA and PCI DSS and serve as an official record businesses can use to prove they were in compliance with the law. For many businesses, it’s necessary to share logs with auditors on a regular basis, especially if an issue occurs. Using audit logs to comply with regulations can protect businesses from major fines and penalties.
Gaining insight
Audit logs record how often someone accesses a certain record or asset, which can give a company invaluable insight. For example, you can use a log audit to learn about user activity, which could be used to boost efficiency, security and performance.
Network engineers, helpdesk staff, developers, and administrators are likely to use these logs internally to boost performance, increase accountability, and keep the system stable. This is because log files provide historical visibility into activity, so changes won’t go overlooked.
Filterable, exportable format
Events are stored in JSON, and contains the following information:
the date of the event;
the user who performed the action;
its role at that specific point in time;
the environment where the action took place;
the complete request/response HTTP payload.
Here's an example:
{ "id": "01FC31EHYYR0MF7J7GEJK2TFM0", "type": "audit_log_event", "attributes": { "action_name": "items.update", "actor": { "type": "account", "name": "servizi@datocms.com", "id": "42011" }, "role": null, "environment": { "id": "new-use-cases", "primary": true }, "request": { "path": "/items/49955591", "id": "e2b2cceb-a4ff-433f-8726-bf2b4da5b33d", "method": "PUT", "payload": { ... } }, "response": { "status": "200", "payload": { ... } } }, "meta": { "occurred_at": "2021-08-02T08:59:54.000+00:00" }}You can easily filter the interesting events via UI using an SQL-like syntax:
# Return actions of type 'items.update'action_name = 'items.update'
# Return actions performed by a collaboratoractor.type = 'user'
# Return actions performed by a specific collaboratoractor.type = 'user' AND actor.id = '4845293'
# Return publishing actions for the record 239408request.path = '/items/239408/publish'
# Return all record creations for the model 855832action_name = 'items.create' AND request.payload.data.relationships.item_type.data.id = '855832'Accessible via API
Enterprise admins use specialised tools called SIEM (Security Information and Event Management) to ingest audit logs and provide search, grouping, and visualisation.
For this reason we made our system very easy to plug in any SIEM by providing a complete API that offers the full history of your project's events.
Try Audit Logs now!
Audit Logs is a feature enabled only for Enterprise customers. If your company is interested in this feature, please contact our Sales team for more details on pricing, we'll be happy to offer you a one-month trial.


